How to secure android phones from hackers 2024
Today’s smartphones receive extensive and sensitive information from their users, the most important of which are user account data, emails, bank information, images, videos, etc. Unfortunately, Android devices have serious weaknesses in terms of security and are considered a suitable target for malware, spyware, and ransomware. In this article, we will mention some practical tips to improve the security of Android phones, which can help protect the privacy and data protection.
How to secure android phones from hackers
Devices based on the Android operating system account for 70% of the global smartphone market; But despite the high popularity, Google and the manufacturing companies have not been able to provide security of the owners of such products well. Although there has been a special focus on improving security features in recent versions of Android; But still, Apple products like iPhone are much more secure.
The weak security of Android devices has caused users to take preventive measures. These can include using security applications, paying more attention to installing programs, or visiting website pages. Below are some of the most important points about this issue.
1. Use two-step authentication
One of the best ways to secure user accounts is to use two-factor authentication. Many services provide this feature to their users by compulsion; while others still provide it as optional. There are various methods for two-step authentication, among the most popular of which, you can mention sending a verification code via SMS, email, or specific applications.
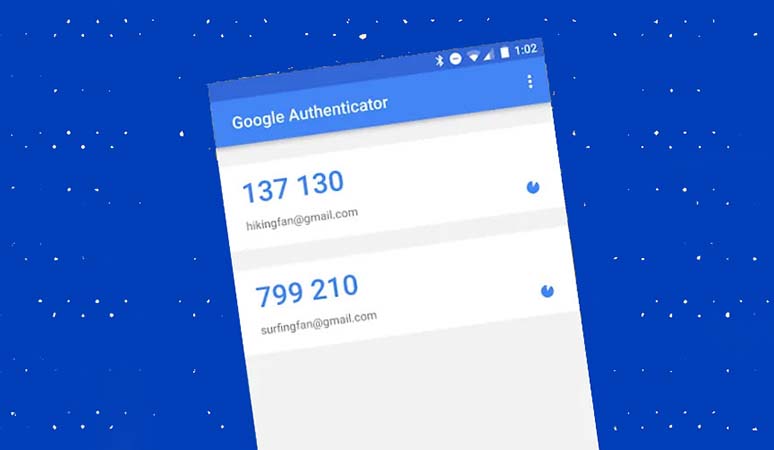
Because most of the information on Android devices is stored on the Google account, we recommend that you enable two-step authentication for it. Of course, if you are interested, you can activate the mentioned feature for other services such as Samsung or Xiaomi accounts.
The Google Authenticator app is one of the best apps to take advantage of the said feature, which is available to users for free.
https://play.google.com/store/apps/details?id=com.google.android.apps.authenticator2&hl=en&gl=US
2. Download programs from reliable sources
Many malware are installed in the form of malicious applications on Android devices with the user’s permission; While their appearance indicates a simple game or tool. Of course, users can reduce the possibility of such an occurrence by downloading the application only from reliable and official sources, in addition to preventing the installation of the application from other sources.
The best source for downloading Android applications is Google Play, But users can also use other stores such as Galaxy Store or Mi Store. Of course, there is also the possibility of malware in these resources; But compared to app download sites, it is less. Not to mention that cracked apps can also be considered a big security risk.
3. Improving the security of Android phones with antivirus
Although Google Play uses an internal scanning engine to check and find infected applications; users can also go to mobile antivirus programs for more certainty. Of course, most of these programs do not provide much special functionality, and users who observe the security issues correctly, will not need a mobile antivirus.

Famous and reliable antiviruses such as Norton, Bitdefender, and McAfee also have versions for Android, some of which are available for free with limited features. Also, if you care about your security while surfing the web and using online tools, you can use the “Sophos Intercept X” application, which is available for free.
https://play.google.com/store/apps/details?id=com.sophos.smsec&hl=en&gl=US
4. Activate the Find My Device feature
Android’s “Find My Device” feature allows users to remotely control their phone or tablet and erase the data on it if needed. This feature can be very useful when the device is stolen or lost and protects users’ data.
To activate the said feature on Samsung devices, just follow the steps below.
- First, enter the “Settings” section of your mobile or tablet and then refer to the “Biometrics and security” section.
- Click on the “Find My Mobile” option and then on the opened page, activate the top button.
- Next, activates the “Remote unlock” and “Send last location” options, which are used to remotely lock the device and send the location, respectively.
5. Manage application access
Applications installed on Android devices require different types of access to function properly. These accesses can include sensitive things such as reading and writing information on the internal memory, viewing calls and text messages, accessing the contact list, etc.
Fortunately, it is not possible to obtain such access without user approval, but it is possible for people to grant access without much consideration.
To prevent misuse of applications, it is better to check the access list after installing them.
For example, an offline game will not need to see text messages or make calls, and if there is such an option, you should suspect it. Google Play uses the internal feature to remove access to unused programs, which you can activate through the following path.
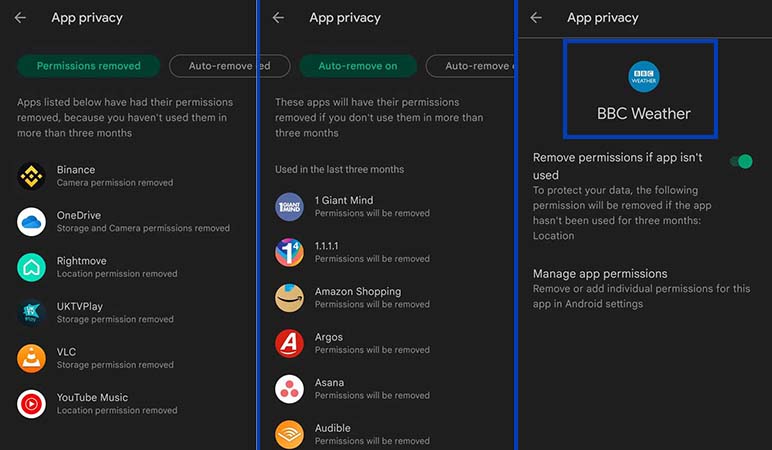
- First, enter Google Play and then click on your profile icon in the upper corner of the screen.
- Next, select the “Play Protect” option and then go to the “Settings” section.
- On the settings page, click on “Permissions for unused apps” and after selecting the desired application, turn the key in the middle of the screen to active mode.
6. Avoid rooting the device
Many Android users root their devices in order to benefit from more applications or features related to personalization. Although rooting alone does not harm the security of Android phones and tablets; apps with root access can have much more control over the device’s performance, which is dangerous in some cases.
Security researchers emphasize that rooted devices are more likely to be infected with malware; As a result, it is better for users to avoid rooting them.
7. Not connecting to insecure and anonymous networks
Publicly available wireless network hotspots have always been considered one of the biggest security threats. Such networks usually have low security; As a result, there is a possibility of using them for unauthorized access to other people’s data.
Frequently asked questions about Android phone security
- What is the best free antivirus for Android devices?
Various antiviruses have been published to ensure the security of Android phones, among the best of which Avast and Norton can be mentioned.
- What is the best app for two-step authentication on Android?
The free Google Authenticator app is one of the best two-step authentication apps used to improve the security of Android phones and user accounts.
- Does rooting compromise the security of the Android phone?
Although the rooting process alone does not harm Android devices; applications with root access can have a much more impact on the functions of phones and tablets.
- Do Android devices need antivirus?
Most Android antiviruses do not have a very special function; As a result, if you follow all security measures correctly, you probably won’t need such programs.
In this article, we talked about “How to secure android phones from hackers” and we are waiting for your experiences to use these methods. Please share your thoughts with us.

